Surely, the “greatest democracy in the world” should not leave any room for doubt about the integrity of its elections. Yet presidential elections in the U.S. are now reflexively met with conspiracy theories, and the past two have been mired with allegations of rigging. And three weeks after the new president was inaugurated, and as far as the public knows, swing states have still not conducted the post-election audits recommended by the Cybersecurity & Infrastructure Security Agency (CISA).
The issue is not that the 2024 election results show signs of being rigged, or illegitimate in any way. The issue is that some cybersecurity experts believe interference in the electronic voting system would be possible without detection—unless a simple audit is completed. It’s not an unreasonable ask: Such audits were conducted after the contested 2020 election and, after 2024, both North Carolina and Wisconsin launched them, though the results are not public.
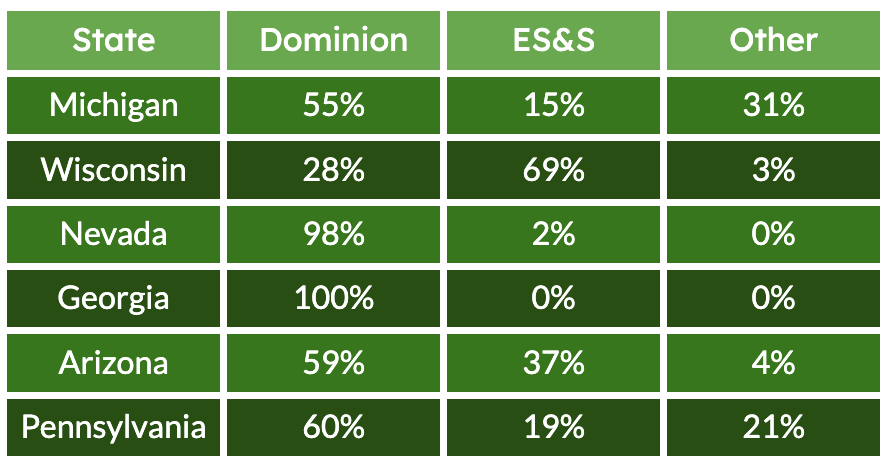
Dominion and ES&S software is used to count 70% of votes nationwide—including Wisconsin, Michigan, Georgia, Arizona, Nevada, and Pennsylvania, all important swing states. The experts call for audits in swing states with paper ballots: Michigan, Nevada, Wisconsin, and Pennsylvania. The concern is this: We know through court documents that copies of the Dominion voting system in Georgia were made by technicians hired by attorneys representing Donald Trump in his quest to question the 2020 election. A similar probe took place in Michigan; those court proceedings, concerning security breaches of ES&S systems, are expected in 2025.
CISA, also known as America’s cyber defense agency, is one of the many agencies under threat of defunding by the Trump administration. CISA is housed within the Department of Homeland Security (DHS). During Kristi Noem’s Homeland Security Secretary confirmation hearing, she expressed, “CISA needs to be much more effective, smaller, much more nimble.”
On November 13, 2024, a small team of computer scientists and election security experts sent a letter to Kamala Harris describing the serious security gaps that may have threatened the integrity of the election—and have the potential to affect future national elections if they are not addressed. Copies of the voting system software—like those made by the team of Trump operatives in 2021–could be used to determine vulnerabilities and “develop malware designed to be installed with minimal physical access to voting equipment by unskilled accomplices to manipulate vote counts.” Again, there is no actual evidence this happened during the 2024 election—but the point is that “under the current circumstances when massive software breaches are known and documented, recounts are necessary and appropriate to remove all potential doubt and to set an example for security best practices in all elections.”
This group of experts has no part in a duty to warn letter sent to Kamala Harris and later debunked by Snopes. That first letter fueled conspiracy theories surrounding the 2024 election results. This November 13th letter, by contrast, explicitly states there is no evidence of fraud; the issue is that “massive software breaches are known and documented,” the experts argue. That is why the group insists “recounts are necessary and appropriate.”
Unless the electronic vote is cross checked with paper ballots, it would be easy for an attack to go undetected, Duncan Buell Ph.D. told Drop Site News. “If they were to insert a hack, they would also insert the code that would delete the hack on the way out the door and we would never, ever see it.” he said. Buell, an author on the letter and Chair Emeritus in Computer Science and Engineering at the University of South Carolina, continued: “I'm thinking of, you know, nation state actors, the Koreans, possibly even a couple of Russian companies that do this kind of thing.”
The letter builds off the recommendation by CISA to conduct post-election audits of physical ballots. On June 3, 2022, CISA released an advisory detailing Dominion’s security vulnerabilities and what election officials can do to “reduce the risk of exploitation of these vulnerabilities.” The advisory concludes with the following recommendation:
Specifically, for each election, election officials should… Conduct rigorous post-election tabulation audits of the human-readable portions of physical ballots and paper records, to include reviewing ballot chain of custody and conducting voter/ballot reconciliation procedures. These activities are especially crucial to detect attacks where the listed vulnerabilities are exploited such that a barcode is manipulated to be tabulated inconsistently with the human-readable portion of the paper ballot.
Cait Conley, a senior advisor at CISA, told Drop Site that "CISA releases dozens of advisories each year regarding software vulnerabilities in all kinds of products. We have no evidence that these vulnerabilities have been exploited and no evidence that they have affected election results in any election, including 2022 or 2024. We develop security guidance for election systems and these recommendations and practices include physical security measures, proper chain of custody, rigorous post-election audits, and pre-and-post-election validation procedures. These measures help identify vulnerabilities in voter registration and election processes that mitigate the associated risks in both the physical and cyber space."
The relationship between CISA and election administrators varies across states. In Georgia, Chief Operating Officer at the Secretary of State office, Gabriel Sterling, spoke to this in his Curling v. Raffensperger testimony.
Q: Do you or do you not — as the most senior official here in the Secretary’s office, do you or do you not rely on CISA to any degree to help you determine appropriate cybersecurity protocols as one of the key factors you identified in election security?
Sterling: Do we rely on them? Rely implies that whatever they say you do. We do not rely on them that way. They inform our decision-making by their own suggestions and basic information of cybersecurity for systems across the country, which vary greatly.
Following the 2020 election, Trump and his lawyers began a rogue probe into whether there had been voter fraud in Georgia and Michigan. To be clear, cyber security experts, including some of the authors on the November 13th letter, see the 2020 election as the most secure election we have had. The 2020 “Big Lie” conspiracies actually led to widespread post-election audits, which confirmed the accuracy of the election outcome.
But, on January 7, 2021—two months after Trump’s loss and the day after the storming of the Capitol on January 6—Trump operatives gained access to Dominion Voting Systems software in a move that has since been scrutinized by Georgia prosecutor Fani Willis. Sidney Powell, one of Trump’s attorneys who was indicted alongside the former and current president, hired a team of data experts to copy voting system software in Georgia.
Court records of emails between Powell and the firm, Sullivan Strickler, show they were hired to collect what they could from “Election/Voting machines and systems.” Video surveillance captured the team at the Coffee County Elections Office. Sullivan Strickler reported their work was successful, and everyone was helpful. Court documents show Sullivan Strickler then shared copies of EMS servers, Tabulation Systems, a “Dominion supplied laptop,” ballot images, and more. (More details are further down in the piece for people who want the extremely detailed backstory here.)
“The threat posed by the theft of voting system software is a serious one, yet it has been conspicuously under-acknowledged by both parties,” Marilyn Marks explained to Drop Site. The lack of action has “left voters in the dark about the shocking vulnerabilities in the system, left wide-open for exploitation.”
Marks spearheaded the Curling v. Kemp lawsuits against Georgia’s election officials to remove unreliable touch screen voting systems, and is the Executive Director of Coalition for Good Governance, a non-partisan non-profit dedicated to evidence-based elections and government transparency.
“We know the entire system was taken. I won't use the word stolen. That's a little litigious, but taken from Coffee County by supporters of the losing candidate in 2020. And everything was put up on the web and they don’t even really know who downloaded it,” Buell said. “My concern with both the ES&S and Dominion leaks is that the bad actors that we have to assume have access to this code are probably pretty good.”
The team of experts, which also includes David Jefferson Ph.D., Lawrence Livermore National Laboratory, Election Integrity Foundation; Susan Greenhalgh, Senior Advisor for Election Security at Free Speech For People; Chris Klaus, Chief Executive Officer of Fusen World; William John Malik, Malik Consulting, LLC; Peter G. Neumann Ph.D., Chief Scientist, SRI International Computer Science Lab; and Professor John E. Savage, Ph.D, An Wang Professor Emeritus of Computer Science, Brown University, calls on Kamala Harris to initiate a hand recount of physical ballots in Michigan, Nevada, Wisconsin, and Pennsylvania. Marks told Drop Site the goal of the recount is “to ensure the outcome accurately reflects the will of the people.”
The copied software from Georgia is not only still being used -- it is the same software voting systems rely on across the country. Dominion systems are used in Arizona, Michigan, Georgia, Wisconsin, Pennsylvania, and Nevada. While there is no evidence the ES&S software was copied or manipulated, there is evidence voting tabulators manufactured by ES&S were accessed by unauthorized personnel. It is unknown what, if any, security updates have been made to voting systems since the breaches. Drop Site reached out to both ES&S and Dominion for comment. ES&S did not answer whether the software in Michigan is identical across other states relying on ES&S voting systems. Dominion did not respond.
In fact, the majority of ballots cast in the U.S. are counted by Dominion and ES&S machines.
These figures were outlined in the letter by Free Speech for People to Harris, and are the result of Verified Voting’s regular election data analysis.
On September 30, 2024, cybersecurity expert Clay Parikh went through a step-by-step demonstration on how to obtain and decrypt Dominion voting systems’ passwords during court testimony in the DeKalb GOP v Raffensperger case. Parikh revealed that Dominion has a hard-coded administrator password that is the same on every Dominion system he has looked at, and has not been changed since at least 2010. When asked what could be done with an admin password, Parikh replied “You could basically do anything you wanted to.”
Marilyn Marks points out that “Democrats have been reluctant to draw attention to the issue, fearing it might suppress voter turnout.” On the other side of the aisle, “Republicans have avoided addressing the troubling reality that senior allies of Trump authorized access to and distribution of this software in 2021 as part of a coordinated effort leading up to the 2024 election.”
Drop Site reached out to Secretaries of State offices for comment on whether the steps to mitigate identified security vulnerabilities outlined by CISA in 2022 were addressed prior to voting in the 2024 election, and whether or not the recommended audit of physical ballots recommended by CISA is underway. They have yet to hear back from officials in Michigan, Pennsylvania, Arizona, Georgia, and Nevada.
Even in Wisconsin, where state law requires the completion of a post-election audit of all voting systems, the results have not been published. The city of Kenosha put out a press release that simply reports their audit was complete as of November 25, 2024, and no discrepancies have been found. It finishes with a link labeled “Information about audits generally can be found here” which renders a 404 error.
The North Carolina State Board of elections responded with the following link, saying, “our canvass documents, including the post-election audit reports, are available here.” However, the page is not publicly accessible. Clicking on the link brings up a window prompting a login. When asked about how the potential ES&S software was accessed during the breach, and if any related security vulnerabilities had been addressed prior to early voting in 2024, NCSBE told Drop Site: “We are looking into this and will get back to you.”
That’s the story if you have time. But we have more details—including the tick-tock of how the Trump team acquired copies of Dominion software—below.
The Breach: A Timeline
Georgia and Dominion
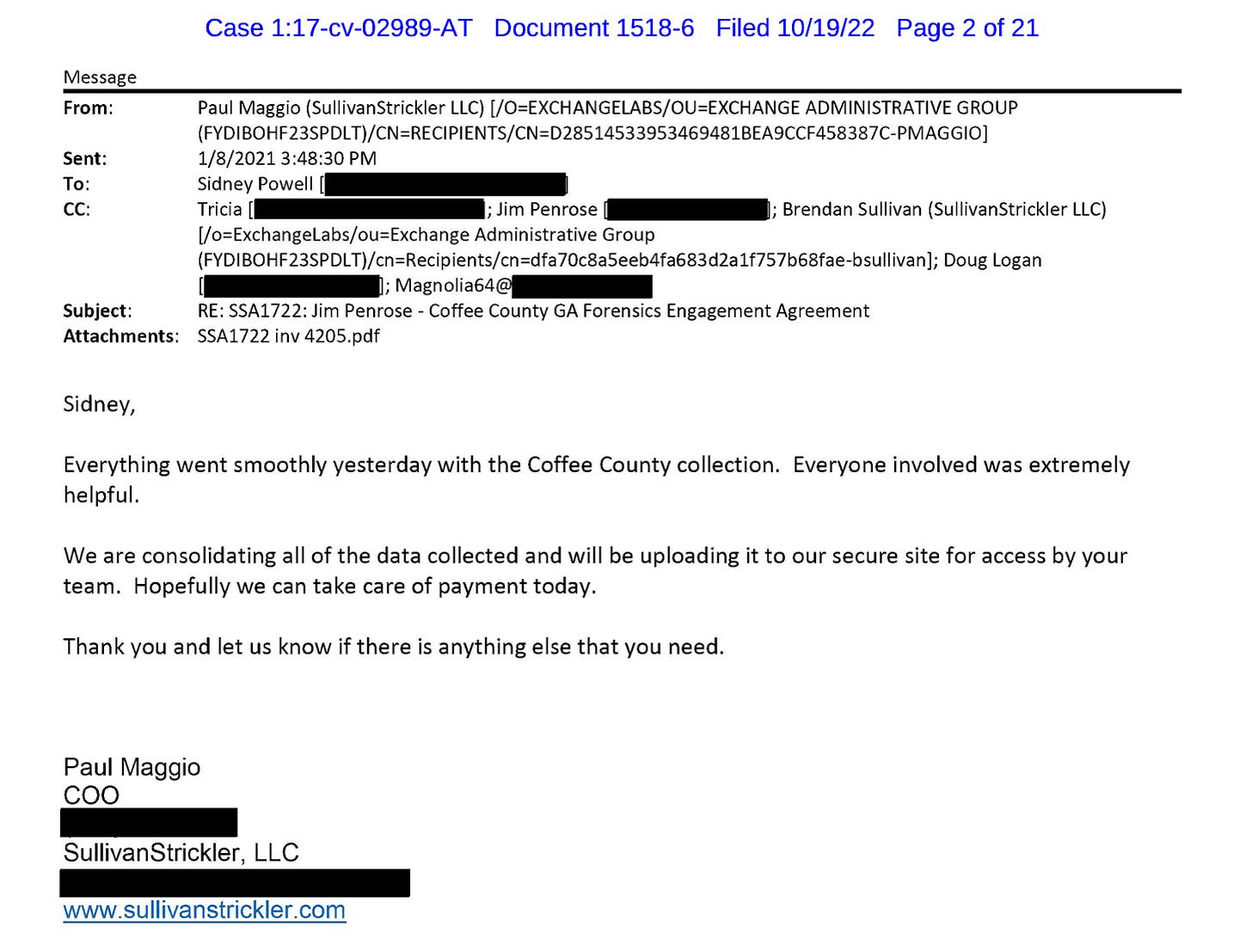
On January 7, 2021, according to evidence presented in court, a team of computer scientists from Sullivan Strickler data solutions was hired by attorneys for Trump to make forensic copies of Georgia’s statewide voting system after Trump made claims that the vote in Georgia had been rigged. That morning, Chief Operating Officer of Sullivan|Strickler Paul Maggio emailed Sidney Powell, “Per Jim Penrose’s request, we are on our way to Coffee County Georgia to collect what we can from the Election/Voting machines and systems.” Jim Penrose is a cybersecurity expert with 27 years of experience, including at the NSA and CIA.
Security footage of the Coffee County Elections Office reveals that at 12:37 p.m., Cathy Latham, then chair of the County Republican Party, was with Maggio and two other people at the office. The court documents include photo stills of the surveillance footage, which show Coffee County’s election official Eric B. Chaney was present at the field office also on January 7, 2021. The latest timestamp on the surveillance footage stills is 6:19PM.
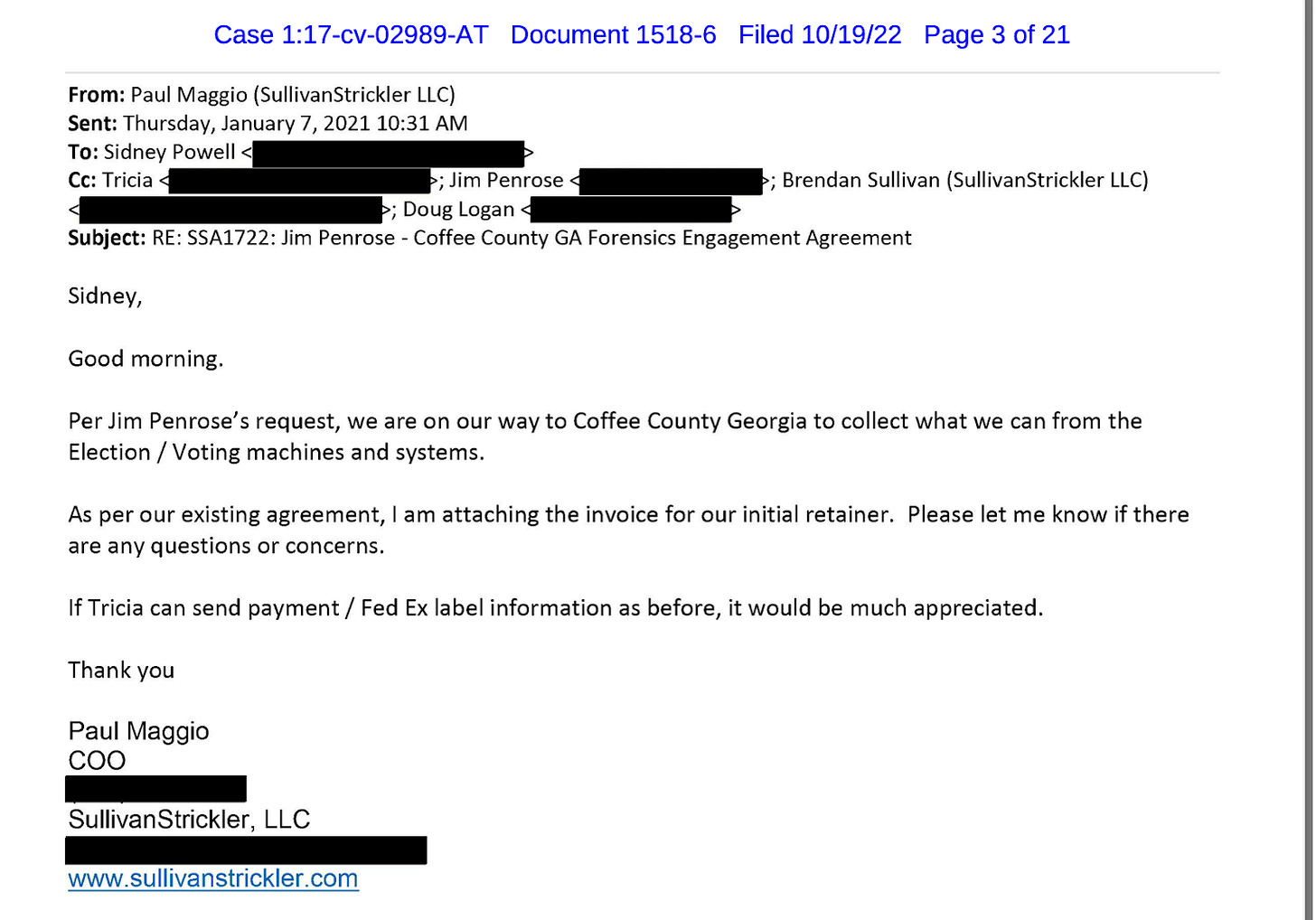
On January 8, 2021, Maggio wrote in an email, “Everything went smoothly yesterday with the Coffee County collection. Everyone involved was extremely helpful,” he informed Powell. “We are consolidating all of the data collected and will be uploading it to our secure site for access by your team.”
Maggio’s hard drive contained “forensic images of an election management system server.” The court obtained a list of IP Addresses that have downloaded and email addresses that have accessed what Sullivan and Strickler obtained from the Coffee County office. The contents include: ballot images, EMS servers, a folder named ‘Dominion-supplied laptop’, Tabulation System, and flash drives from the election office. Court exhibits also include photos of a precinct tabulator, compact flash cards, thumb drives used to program tabulators, touchscreen voting machines, a computer used to check in voters and a laptop computer supplied by Dominion.
The voting security expert, Kevin Skoglund, told the court, “after a review of the documentary evidence” he concluded that in “2021, the security of Georgia’s voting system was breached in Coffee County on at least three occasions: January 7, January 18-19, January 25-29.” He described this as, “by any measure a consequential breach of Georgia’s election security.” Skoglund explained that the copied software from the Coffee County election office “includes protected software from almost every component of Georgia’s election system.”
On January 19, 2021, two men hired by President Trump’s attorneys discussed what to do with the data and software. “Here’s the plan. Let’s keep this close,” former NSA official Jim Penrose texted Cyber Ninjas CEO Doug Logan. The texts obtained by CNN go on to reference the Georgia runoff. Penrose said, “We only have until Saturday to decide if we are going to use this report to try to decertify the Senate run-off election or if we hold it for a bigger moment…”
Sullivan|Strickler claimed its work was done under the direction of attorneys, and did not deny their work making copies of the Dominion voting system in Georgia. In August 2022, the attorney for Sullivan|Strickler, Amanda Clark Palmer, made the following statement: “Sullivan|Strickler was retained by and took direction from licensed, practicing attorneys to preserve and forensically copy the Dominion Voting Machines used in the 2020 election … The firm had no reason to believe that, as officers of the court, these attorneys would ask or direct Sullivan|Strickler to do anything either improper or illegal.”
Michigan and ES&S
Jim Penrose and Doug Logan are implicated in a similar scheme that unfolded in Michigan between January and June 2021. Paul Maggio of Sullivan|Strickler was hired to help again, and the work in Michigan was referenced in the same email chain entered into evidence in Georgia. In coordination with former state Rep. Daire Rendon, and attorneys Matt DePerno and Stephanie Lambert Juantila, Maggio’s team took ES&S equipment—breaking open the security seals on voting tabulators—according to an investigation conducted by the Michigan Attorney General’s office.
Two letters, both dated August 5, 2022, detail some of the findings. One was sent to Secretary of State Jocelyn Benson by Deputy Chief Attorney General, Christina M. Grossi. The other letter was a petition to appoint a special prosecutor, sent by Danielle Hagaman-Clark, the Criminal Trials and Appeals Division Chief.
Grossi’s letter reveals the investigation found unauthorized access to ES&S voting systems that “occurred between the dates of March 11, 2021, and late June of 2021.” Hagman-Clark’s petition details the following: “5 tabulators were taken to hotels and/or AIRBNB’s in Oakland County where Lenberg, Cotton, Penrose and Logan broke into the tabulators and performed ‘tests’ on the equipment. It was determined during the investigation that DePerno was present at a hotel room during such ‘testing.’”
On April 7, 2021, a subpoena was issued to Verizon “to produce detailed information concerning specific devices.” Verizon produced the modem ID numbers on the devices, revealing they were ES&S tabulators. Deputy Attorney General Grossi wrote: “These ID numbers are those of voting tabulators manufactured by ES&S.”
Deputy Attorney General Grossi wrote that in March 2022, “ES&S subject matter experts confirmed that there was an attempt to access the internal components by unauthorized personnel.” ES&S then conducted an analysis on their equipment and “found no evidence” of “any software or firmware manipulation of the device” nor “that any of the secure, encrypted USB thumb drives were subject to any unauthorized access or any software/firmware manipulation.”
ES&S told Drop Site: “To our knowledge, there is no evidence that any ES&S proprietary election software from Michigan has been acquired or shared illegally”—though, as Buell pointed out, such evidence wouldn’t necessarily exist.
ES&S told Drop Site about changes made since 2021. “All seven ES&S customer counties in Michigan, along with many other U.S. customers, have upgraded their election management software since 2022 as part of a normal upgrade process,” they said. ES&S did not specify which customers upgraded their software, nor what has been changed. “ES&S systems are also paper-based systems, with a voter-verified paper record which allows jurisdictions to perform tangible and statistically valid post-election audits.”
While the legality of accessing voting systems has been a litigious topic, the alleged unauthorized tampering with ES&S tabulators in 2021 is expected to be explored in court.
How to Hack a Voting Machine
In 2017, a cybersecurity and voting system expert demonstrated during court testimony how to take control of one of the Georgia voting machines without violating any security protocols, or damaging the “tamper evident security seals.” Dr. Alex Halderman used a ballpoint pen to reach a button within the screen, a fake voter card, and a USB device connected to a printer. He was able to rewrite the touchscreen’s code with "Super User Access.” The civil case, Curling v. Raffensperger, focused on vulnerabilities with Georgia’s voting touchscreen systems. In September 2018, the court required that Georgia replace 27,000 voting machines. They were replaced with Dominion touchscreen systems with similar vulnerabilities, which led to the case being revisited in a 17-day bench trial January-February 2024.
Dr. Halderman provided a report detailing issues with the voting systems in Georgia. The redacted version is public, but the full version does not sound different from what Halderman shared in court. An individual familiar with the report shared the following with Drop Site: “the unredacted report basically said, here are the 10 or 12 vulnerabilities that a reasonable senior undergraduate computer science student would ask about in a computer security class… and here's how we attack each one of them successfully without really much effort.”
In a deposition for Curling v. Raffensperger on February 11, 2022, Michael Barnes, the Director of the Election Center for the Georgia Secretary of State, was asked the following: “Can you identify one cybersecurity election expert that has endorsed the current Georgia system as a reliable voting system?” Barnes's response was straightforward: “I cannot.”
On September 30, 2024, Clay Parikh demonstrated how to hack into Georgia’s voting systems during testimony in the DeKalb GOP v. Raffensperger case. Parikh, a witness for the Dekalb county GOP, provided a tutorial before the court that was live streamed on YouTube. It is still available to replay on Judge Scott McAfee’s page.
Parikh accessed the system with an AES decryption tool on a public website. Parikh testified, “The massive amounts of vulnerabilities on this system, the poor configuration of the database itself, even if you encrypted that database, somebody mid-level could take over.” He called this an “egregious violation of the basic security principles.”
Simple vulnerabilities in Dominion and ES&S systems have gone unaddressed, Buell said—“both Dominion and ES&S have not bulletproofed their software, in my opinion, to make it hard to make mistakes.” In many states, a paper ballot is filled out by coloring in a bubble next to the name of the candidate the voter choses. When the ballot is scanned, the machine is not reading the ballot as a human would. Professor Buell explained, “The barcode is not ‘candidate and contest name,’ it is the XY coordinates of where the bubble would be for that candidate and contest on a hand marked paper ballot.” If the location of candidates on a paper ballot were misplaced, that would create a false read—an issue that has been known to happen at least once, including in Antrim County, Michigan in 2020. Currently, it is not a regular practice for the paper ballots to be checked against a county-level “cheat sheet” to ensure the layout of candidates is consistent across all precincts, and therefore that the machines read the ballots accurately.
Prior to the 2024 election, issues with systems from ES&S and a third company, iVotronics, have produced double-counting in South Carolina and New Jersey. “The data, the tallies come back on a flash drive. A flash drive is inserted in the county headquarters central computer and the tallies are uploaded.” But there is no official log of the serial number from a flash drive already counted. “So when you insert it a second time, it's happy to upload the tallies again,” Buell explained. When a flash drive already counted is inserted, “there should be a table of serial numbers and when you upload something already there, there should be a pop up window that says ‘Are you sure?’ And apparently that doesn't happen either with ES&S or with Dominion.”
Recount or Post-Election Audit?
While recounts can be both long and costly, every vote does not need to be counted by hand to provide assurance to voters. A statistically significant random sample of ballots can assure voters the results are reliable, by showing the voting systems’ count matches the physical ballots.
An audit would require a hand count of less than one-third the number of votes counted in the 2020 Maricopa County recount. Focusing on swing states recommended in the letter, a reasonable audit would rely on a hand count of 698,777 total votes—a random sample of 175,402 ballots in Wisconsin, 179,030 in Michigan, 164,182 ballots in Nevada, and 180,163 in Pennsylvania. An audit of this size would provide a high level of statistical significance (p<0.01), or a 99% confidence-level, with a margin of error of less than half a percent (+/-0.3%).
The group behind the letter views post-election audits as something that should be standard practice “binding risk-limiting audits (RLAs) or hand recounts should be routine for all elections, especially when the stakes are high and the results are close.”
Regular post-election audits not only deter bad actors, they identify any unusual results in the event of vote count manipulation. Machines that counted the ballots could be assessed for flaws, investigations completed, and election security strengthened for future elections. Hand counts could then be completed to confirm the true results. Wanting votes counted fast is fine, but ensuring the count is accurate is necessary to ensure every election in the United States reflects the will of the people.
Finally, how did Dominion and ES&S come to dominate the voting systems market? ES&S lobbied public officials to invest. So did Dominion. ES&S gave sales pitches across the country; Duncan Buell happened to be in attendance at a presentation in Greensboro, North Carolina. “There were lobbyists who were saying that the paper ballots would cost more than buying the equipment,” he said. Buell did the math; the data showed otherwise. It would take “6 elections countywide for 10 years before the costs meet… Paper is just so much cheaper. That’s not what you hear from the vendors.” Not only are the electronic vote machines vulnerable to cyberattacks and present new opportunities for miscounting, they are more costly than alternatives.







Thank you for this, excellent report! The U.S. needs a national voter's list along with federal elections held under federal rules, rather than the present state/county shambles. And paper ballots!
I made an appeal to some of the swing states' election commissions to conduct these post-election audits, with no response. I'm glad to read that this is usually conducted yet horrified to see evidence of malfeasance from the MAGA ranks in regard to the two most-often used systems. Why aren't states willing to do audits if they believe the results will support the outcome? Having confirmation that the 2024 vote was conducted fairly is essential for future elections.